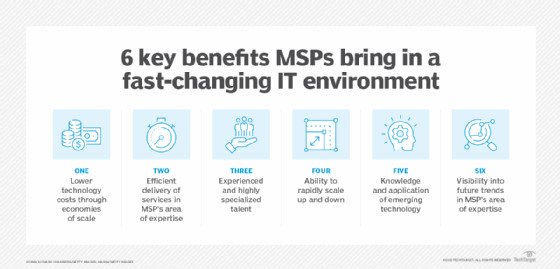
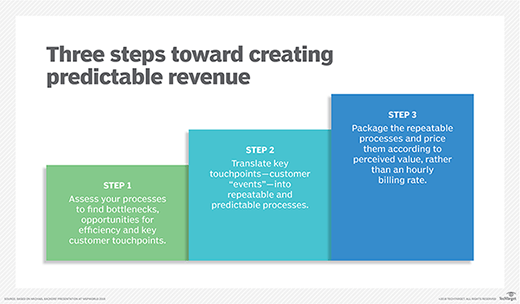
How Kdit Services can Save You Time, Stress, and Money.
You desire the very best for your company, which suggests making certain you have IT service that meets that assumption. If you're expecting frequent on-site gos to, it's because you intend to make certain whatever is being dealt with in a timely style. As well as it's most likely the level of solution you have actually called for previously, either from an internal IT person or an outsourced designer.
They do have a method to ease your anxiousness concerning the functionality of your IT setting. The objective of taken care of services is to allow your organization's success via innovation. To do this, your MSP should not just sustain the IT you utilize but take positive measures to consistently reduce the number of tech troubles you experience.
Your designer takes a lengthy time to resolve issues with said service. By carrying out present, assistance options, you resolve the root of your issues associated to outdated applications.
Little Known Facts About Kdit Services.
If you do not intend to upgrade your out-of-date IT framework, your MSP will frequently be functioning around obstacles. Ultimately, managed IT solutions may not make the most sense for your service if this holds true. When you choose to move forward with locating an MSP for your organization's IT, you'll have to find one that is a great suitable for your company.
If the carrier you had in mind can't address your demands, ask what solutions they could supply or if they could advise an additional supplier. Managed solutions might not be problem-free, but they are an excellent option for services looking to outsource their IT solutions. If you're bothered with on-site availability, degree of support, updating aging framework, finding the appropriate MSP, or the dozens of various other concerns you may have, ensure you discover a technology providers that resolves your concerns.
Or if you aren't certain managed services are the right selection for you, download this totally free IT Solutions Quick Guide to aid you establish which type of technical support will certainly function best for your organization.
Self-help details and also documentation from UW Infotech (UW-IT) concerning modern technology tools, solutions and also resources is on this web site, IT Connect. Inspect out the typical jobs below to locate solution to one of the most regular reasons UW pupils, faculty and also personnel need aid from UW-IT, or scroll down for how to speak to UW-IT.
The Definitive Guide for Kdit Services


For faster support, contact UW-IT via the kind on the base of this page or by phone. If you still require in-person support, please book an appointment with the UW-IT Service Facility.
Welcome to IT4Faculty, the Details Modern Technology (IT) Providers for Professors internet site. Our website is customized to provide fast IT details and help for professors. The Info Innovation (IT) Department is dedicated to offering the highest feasible degree of solutions to the university community. Questions as well as remarks are constantly welcome; please phone call (806) 742-4357 (HELP) or open up a new issue with ask, IT.
IT solution administration-- usually referred to as ITSM-- is merely just how IT teams handle the end-to-end shipment of IT solutions to consumers. This consists of all the processes and also activities to make, develop, deliver, as well as assistance IT services. The core idea of ITSM is the idea informative post that IT need to be delivered as a service.
You would submit your demand via a portal, completing a ticket with all appropriate info, as well as beginning a repeatable process. The ticket would certainly land in the IT team's queue, where inbound requests are sorted as well as attended to according to relevance. Due to their day-to-day interactions with IT, individuals often misunderstand ITSM as fundamental IT support.
The Definitive Guide for Kdit Services
There is a typical line of thinking in the IT sector that assumes that a correct technique to ITSM must comply with three action in this order: 1) Construct as well as execute IT innovation. 2) Generate and also apply the appropriate process. 3) Individuals can discover the innovation and also follow by the process.
For us, We've even developed a team playbook to provide tools that assist groups improve the method they work. IT teams need to be consistently discovering and enhancing. They must really feel valued and encouraged to make a distinction in the company. Rather than responsing to regulations enforced by a tiered coverage framework or stiff process, IT teams can make informed decisions about things like embracing SLAs and also which software application to implement.
IT groups take advantage of a selection of structures to lead their job. The most typical ones we become aware of are ITSM and Dev, Ops, though there are numerous other ideas, like COBIT, SIAM, IT4IT, lean, and also the checklist continues ... So what abbreviations do you require to recognize? Right here we'll cover two of one of the most prominent frameworks for contemporary IT teams-- ITSM as well as Dev, Ops-- in addition to an usual method to ITSM.
IT service management-- often described as ITSM-- is merely just how IT groups handle the end-to-end shipment of IT services to clients. This includes all the procedures and activities to design, create, supply, as well as assistance IT services. The core idea of ITSM is the belief that IT must be supplied as a solution.
8 Simple Techniques For Kdit Services


IT teams need to be constantly discovering as well as enhancing. Instead than addressing to regulations imposed by a tiered reporting structure or stiff process, IT groups can make enlightened decisions concerning things like taking on SLAs and navigate to this website also which software program to apply.
IT teams utilize a variety of structures to direct their job. The most usual ones we read about are ITSM and Dev, Ops, though there are countless various other principles, like COBIT, SIAM, IT4IT, lean, and also the list proceeds - KDIT Services... So what abbreviations do you require to know? Right here we'll cover 2 of one of the most significant frameworks for modern-day IT groups-- ITSM and also Dev, Ops-- together with an usual strategy to ITSM.